A British company which has devised an encryption system for messaging is trying to get the UK government’s GCHQ to give its first-ever approval to an off-the-shelf smartphone app.
And in a bid to demonstrate its security, it is offering a £10,000 reward to any hackers that can crack it.
Called Redact, the company is also offering its £3.99 Secure Messenger app for the iPhone for free to all MPs and has also submitted it to CESG, the UK government’s National Technical Authority for Information Assurance, which tests the security and quality of computers and smartphones. So far CESG has only certified smartphones running BlackBerry’s BB7 operating software as meeting the security requirements for restricted data inside government, based on the difficulty of decrypting or capturing content stored or sent from the phone.
No off-the-shelf app has ever won CESG approval before, but the company is confident that it is more secure than other systems which have already been given clearance for use by the organisation.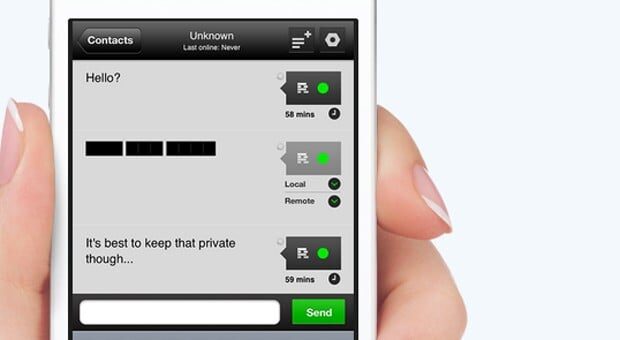
A key failing of systems such as Apple’s iMessage is that despite being encrypted they pass through a company server which could be hacked, says Adam Gibson, a spokesman for the company. “Unlike comparable services like BBM or Snapchat, there’s no traffic through a server. It’s all done peer-to-peer – we like to think it’s an app that could have kept Chris Huhne and Vicky Pryce out of jail.” Huhne and Pryce were convicted of perverting the course of justice after emails and texts they had sent when they were discussing Pryce accepting driving points earned when Huhne was driving were leaked to newspapers.
The Redact Secure Messenger app connects to a server which connects two handsets together over a data connection, and then drops out – leaving the handsets able to converse using triple-encrypted messages.
One extra element to the app’s messaging not found in standard systems is that messages can be deleted from the receiver’s handset as well as the sender’s, even after being sent.
The app doesn’t ask for usernames; instead, users are automatically assigned a PIN, which is not stored by the company. “There is no recovery tool for hackers to exploit,” Redact says. “Only you can change your alias, so you can be certain [that] contacts aren’t using your real name anywhere in the application.”
Going directly between phones eliminates “side channel attacks”, where all sorts of related data is monitored to gain clues about the cryptographic systems and keys used to encode and decode data.
The hacking challenge, at http://www.moderndayturing.com/, challenges all comers to try to crack a message being passed back and forth between two phones at a specified location. “We’re pretty confident it can’t be done, but obviously, we anticipate tons of people trying,” said Gibson. “We figure the longer it stays uncracked, the more secure we are,


















